by Cindy Heffner | May 18, 2021 | Cybersecurity, MDR
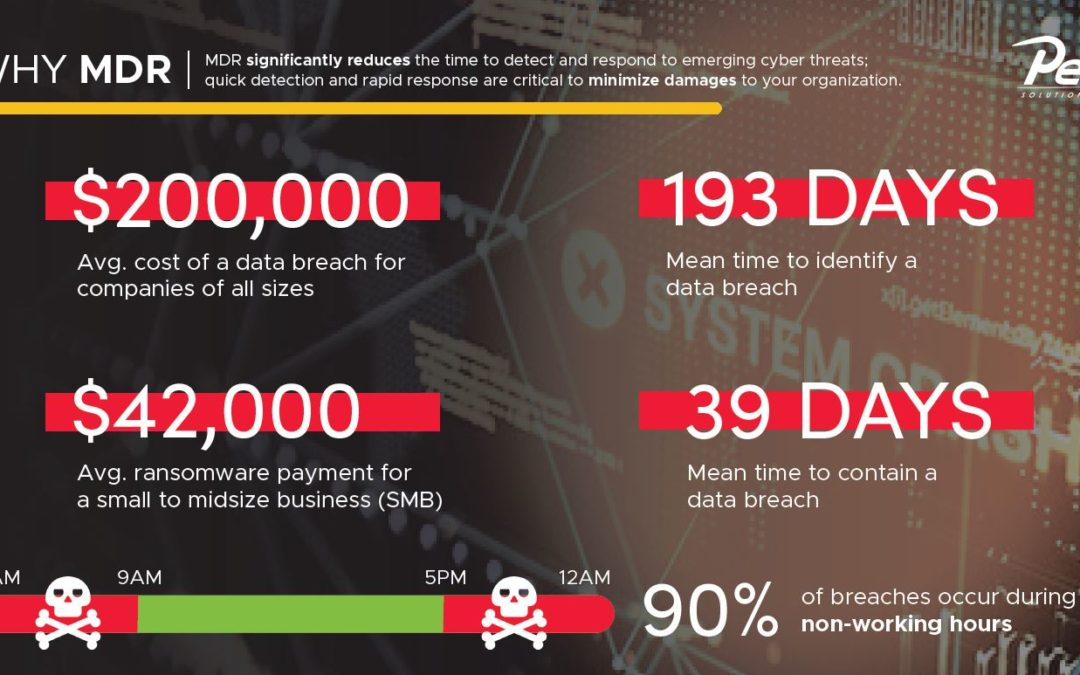
Hopefully, you are already engaged in cybersecurity services that offer security alert monitoring and manage firewalls. While prevention and perimeter protection are important, they are no longer enough to detect and stop cyberattacks on their own. MDR (Managed...

by Cindy Heffner | May 11, 2021 | Cybersecurity, MDR
The statistics on cyber attacks are staggering. 2,244 attacks are initiated by hackers every day and damages from successful attacks are projected to hit $6 Trillion this year. While you may have implemented the basics – backing up your data, patching your...

by Cindy Heffner | May 4, 2021 | Mobile Workforce
With increased scrutiny of public service organizations and their community interactions, many leaders are looking to transparency solutions like equipping their field crews with body-worn cameras. Physical altercations, theft accusations, and malpractice concerns can...

by Cindy Heffner | Apr 20, 2021 | Cybersecurity, Dark Web
There are more than 4.5 billion web pages on the “standard” internet. The entirety of the internet, including the dark web, is estimated to be 400 to 500 times larger! The dark web is content that exists on sites only accessible by means of specific...

by Cindy Heffner | Apr 13, 2021 | Cybersecurity, Dark Web
A Google survey found that about 65% of internet users use the same passwords for multiple services. Such poor password hygiene provides an easy passageway for cybercriminals. Once a password is stolen or becomes decoded by cybercriminals, they can access accounts on...






