
Cybersecurity
You might already know about the escalating cyber threats, from ransomware to hackers; but it is very possible you are underestimating the risk to you and your business. This is not a topic to be casual about. Should a breach occur, your reputation, your money, and your company will be on the line.
Are you confident your IT staff or partner is perfectly managing every area and practice of cybersecurity to keep your business as safe as possible from cyber attack and damages? Use this self-assessment to evaluate your current program. If you cannot confidently check off each item, it may be time for a new IT partner.
Don’t Believe These Myths:
Free is fine
You get what you pay for and the bad actors are recruiting hackers with six-figure salaries. Free software and applications will NOT protect you from today’s sophisticated attacks.
We're small
43% of breach victims are small businesses. Bad actors assume smaller businesses have less precautions in place and therefore make easier targets.
We have anti-virus
Having anti-virus and firewalls in place is an incomplete solution as they cannot distinguish an authorized user from a compromised credential.
Where you might be vulnerable
- Email – reduce exposure that comes through email, which is the most common
- Passwords – making sure there’s an enforceable password policy and routinely search dark web for compromised credentials
- Security awareness training – policies that people are actually aware of and following
- Updates – keep all software current automatically
- Vendors – hold your SAAS vendors accountable by requiring them to have proper cyber protection in place
- Cloud and mobile security – a critical part of how you do business, but also highly vulnerable to attacks
Write down the date of your last risk assessment
We all know that IT is always changing. It’s important to establish a baseline and close existing vulnerabilities and for this to happen on an on-going basis. Cybersecurity should never be “set it and forget it.” If you can’t think of the date when you completed a risk assessment or if you’re relying on solutions from years past, then now is an opportune time to go through the list of risks above and determine the status of your cybersecurity ecosystem. We will help you with this! Schedule a FREE risk assessment.
Think about your customers
Consider the chaos that will ensue after a breach – possible social media coverage, lost customers, angry partners and a damaged reputation. The impact creates a ripple effect, especially if you consider how security is actually a part of your customer’s user experience. Also, customer’s will not be able to access their data because ransomware has locked your system.
It is their data that needs to be protected, whether that is from ransomware or a disgruntled employee. Every business says they value their customers and want to provide a good experience. This starts with protecting their data.
There’s a huge financial stake
Criminals are adept at creating emails that look and seem real to get you or someone on your team to wire money to a phony account. They may get access your data and hold it ransom or they may impersonate a business you actually have a relationship with. The bad guys will go to great lengths to be sneaky and get your to send money — you may even have a conversation with them and not realize it!
You deserve best practice
We understand that cybersecurity can seem complex and expensive. We also know your employees need dependable, quick and secure access to company data and their computers and devices. Our core values are about providing enterprise-grade services to small and mid-size businesses.
We’re really good at working with our customers’ budgets and providing best-practice solutions – because that’s what you deserve.
We follow the National Institute of Standards and Technology (NIST) framework and align your plan with corporate objectives that meet compliance standards and move you away from ad-hoc and reactive security efforts.
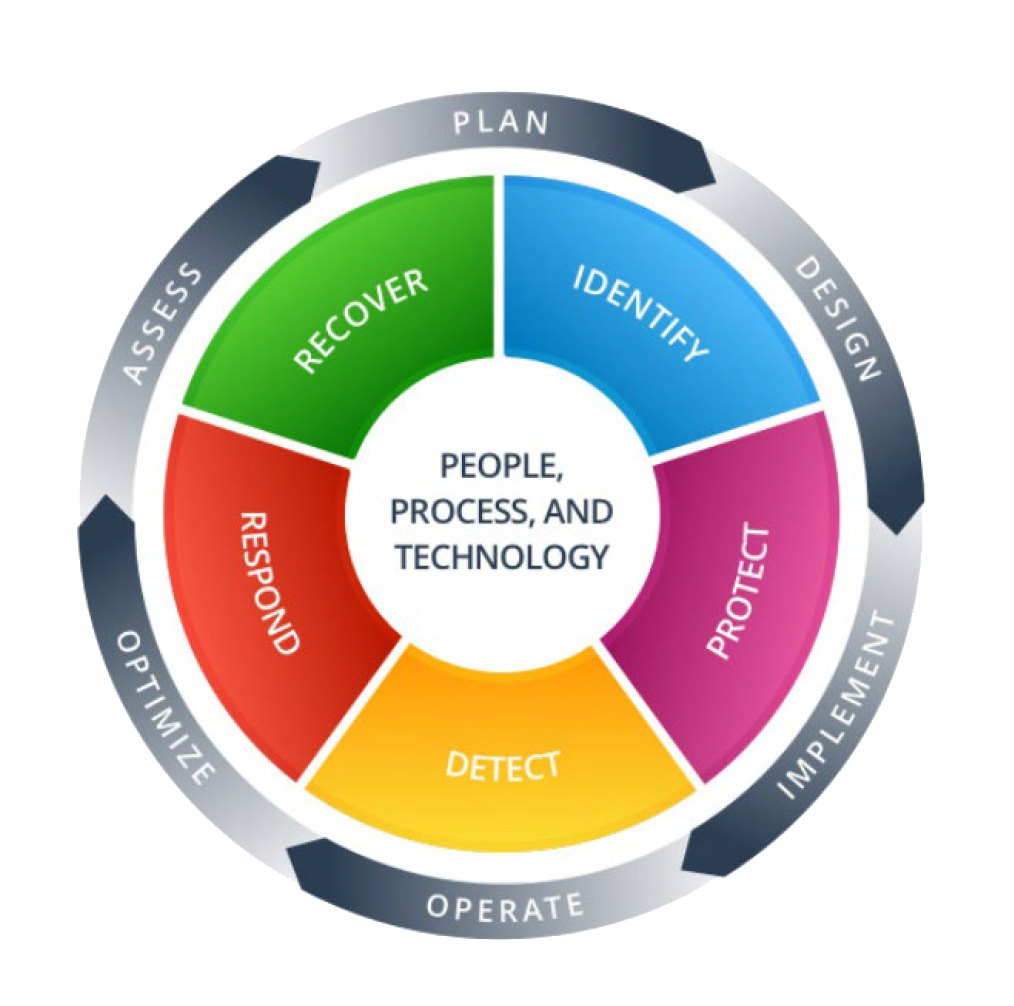
NIST Framework
Pearls of wisdom
“We didn’t understand our vulnerability until an attack on one of our vendors impacted our business. Pearl helped us identify gaps, recommended solutions to improve our security posture, and taught us how to hold our vendors accountable for cybersecurity as well.”
— Jay King, CEO
More Cybersecurity Resources
Mobile App Security Risks: What You Need to Know
Mobile apps are essential tools for business. From managing tasks to communicating with clients, these apps offer convenience at your fingertips. However, they also come with their own set of security risks. Understanding these risks is crucial for protecting your...
Yes, Cybersecurity Matters Even When You’re Traveling
Whether you’re heading to a conference, working remotely from a cozy café, or even on a personal vacation, your sensitive data can be more vulnerable than usual. Here’s why cybersecurity matters even when you're traveling and some simple ways to keep your devices and...
Schedule a Roadmap Assessment
During this brief discussion, you can tell us your concerns and we’ll give you some guidance (for free) about how to improve gaps in your IT strategy.


