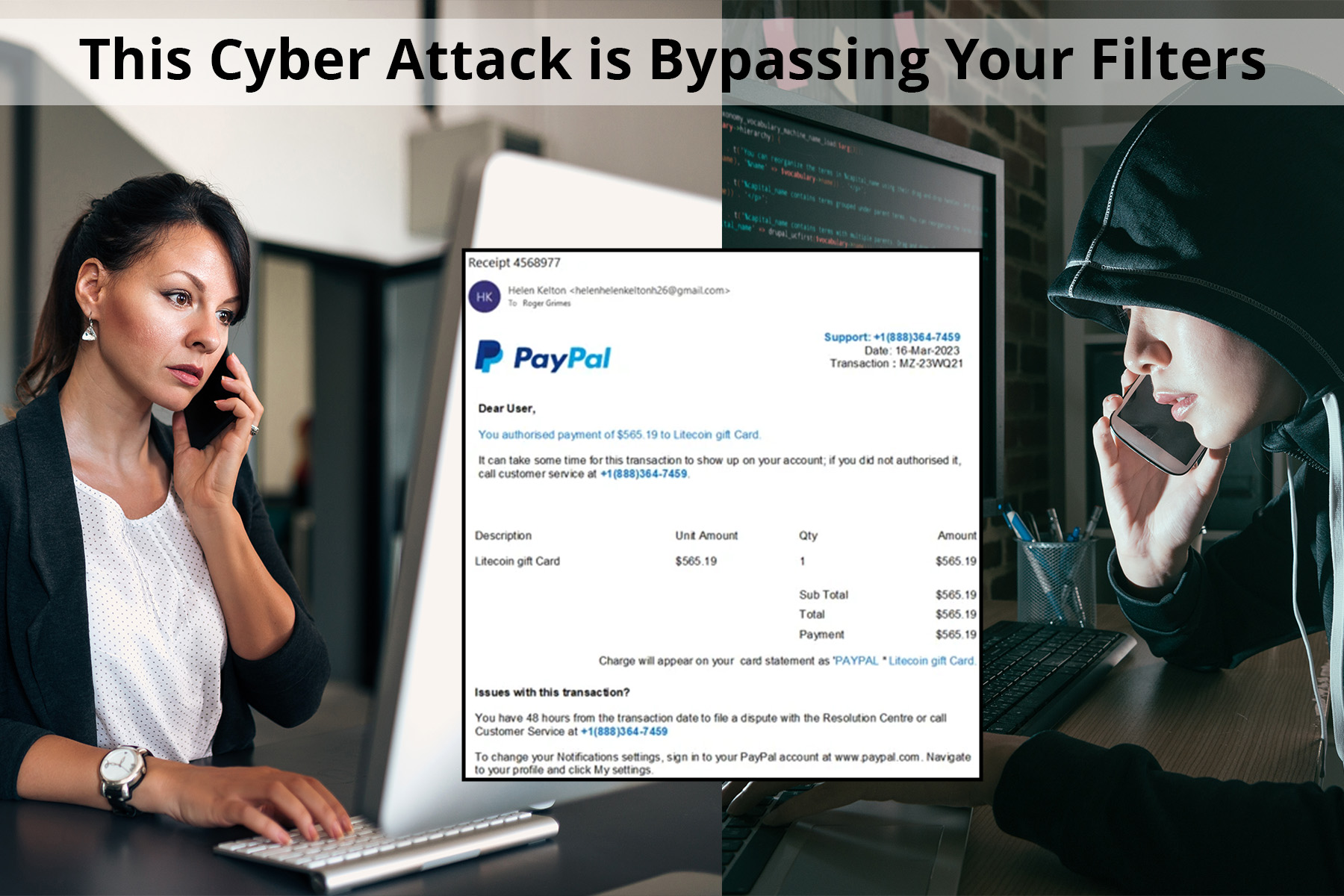
Have you heard of callback phishing? Typically a phishing email contains some sort of message requiring the user’s urgent response. But unlike traditional email phishing, it does not contain a URL linked to a malicious site or content. Instead, it contains a phone number that the user is prompted to call. It has raised the attention of the FBI who issued an alert about this cyber attack method bypassing your filters.
Callback phishing is gaining popularity among cybercriminals because it poses a unique challenge to anti-phishing content filters. With traditional phishing attacks, the anti-phishing content filters can review the sent text and open the URL locations to see if they contain malicious content or code. There are content and objects that can be examined to determine whether or not the email is malicious. Unlike traditional phishing emails, callback phishing messages are presented as a single un-clickable picture file, making it difficult for filters to analyze the content.
When users make the call, they are typically directed to an overseas call center. The scammers behind callback phishing are adept at manipulating victims into installing malicious software or providing data. In some cases, this software could be ransomware, while in generic callback scams, scammers may manipulate users into performing transactions, ultimately stealing money from the victim.
The security awareness of everyone is key to stopping this attack method.
- Educate Your End Users: Start by raising awareness among your employees about callback phishing. Train them to be suspicious of emails that contain only a single picture file, a repeated phone number, and no clickable links.
- Encourage Vigilance: Teach your employees to be wary of unexpected messages that instruct them to perform actions they’ve never been asked to do before. If a message fits this description, advise them to confirm using alternative methods before taking any action.
- Verification Protocols: Implement verification procedures for any unexpected or suspicious messages. Encourage users to verify the legitimacy of such messages by calling the company directly using a known good phone number or visiting the official website directly.
Education is a powerful weapon, and by empowering your employees with knowledge about callback phishing, you strengthen your business’s defenses. If you need help implementing a security awareness training program, reach out to us.