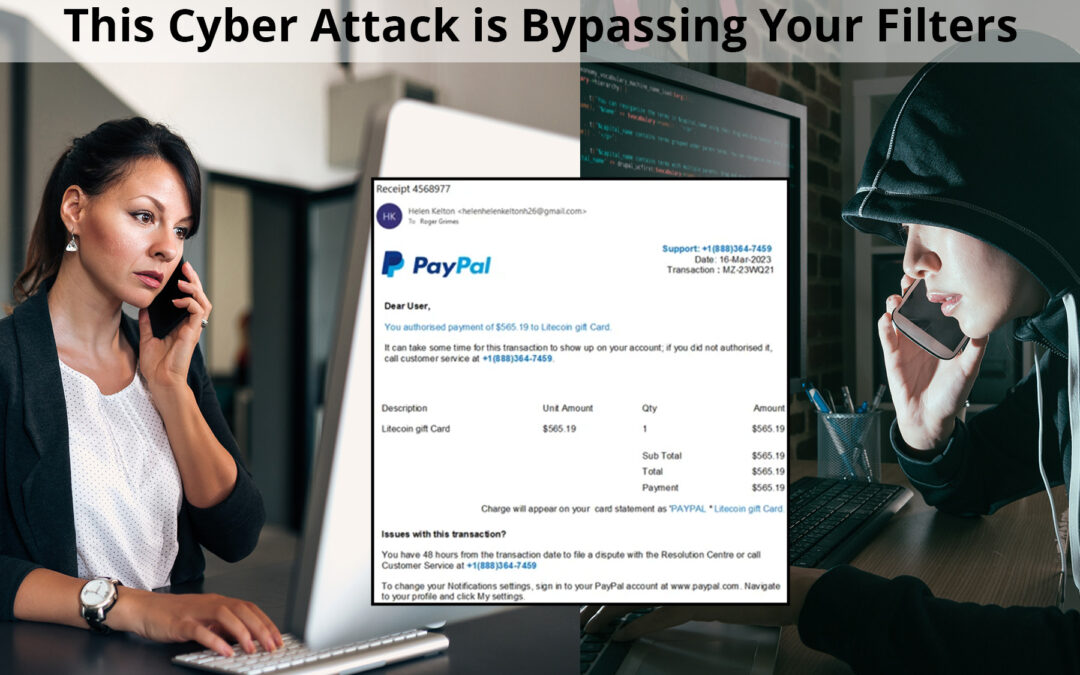
by Floyd Bell | Dec 12, 2023 | Cybersecurity
Have you heard of callback phishing? Typically a phishing email contains some sort of message requiring the user’s urgent response. But unlike traditional email phishing, it does not contain a URL linked to a malicious site or content. Instead, it contains a phone...

by Floyd Bell | Nov 21, 2023 | Cybersecurity
Friday marks the official beginning of the holiday shopping season and no one is more excited than cyber hackers. During this time of year, the opportunities to take advantage of unsuspecting and often overwhelmed holiday shoppers create a playground for bad actors....

by Floyd Bell | Nov 7, 2023 | Professional Services
From customer information to financial records, your company’s data is invaluable so it’s crucial to have a reliable backup strategy in place. Whether to protect data from being compromised or lost due to cyberattacks or to be able to quickly recover from...

by Floyd Bell | Oct 31, 2023 | Professional Services
A reliable and speedy WiFi connection is nothing short of essential for anyone working from home. Yet, we’ve all experienced those frustrating moments when our WFH WiFi decides to slow down, disrupting our work, online meetings, and even our downtime. Say...

by Floyd Bell | Oct 24, 2023 | Cybersecurity
Mobile devices are a lucrative opportunity for bad actors not just for your personal info, but can also be an entry point into the organization you work for. While your organization may have even basic cybersecurity measures implemented for your desktop devices and...






