
by Floyd Bell | Feb 20, 2024 | Managed Services
If your computer takes longer to boot up than it takes to drink your morning coffee, it’s time to give it a little clean-up and TLC. We have five practical tips to speed up your computer and make sure it is charged up and ready to work when you are. Limit...

by Floyd Bell | Feb 6, 2024 | Cybersecurity, Managed Services, Professional Services
Disasters, whether natural or technological, can strike at any time, potentially jeopardizing operations and data integrity. To safeguard against such threats, implementing a robust disaster recovery plan is crucial. One essential aspect of this plan is regular...

by Floyd Bell | Jan 30, 2024 | Cybersecurity, Managed Services
February 1st is Change Your Password Day. While it’s not a holiday that gets you off work, it serves as a good opportunity each year to do a quick check-in and make sure you’re using strong passwords that will keep your accounts protected. The suggested ‘rule’ used to...

by Floyd Bell | Jan 9, 2024 | Co-Managed IT, Managed Services
An efficient IT infrastructure can significantly enhance productivity, reduce costs, and foster innovation. To achieve this optimal performance you’re going to need a plan. This 15 step IT optimization plan will help determine if and where you can be saving...
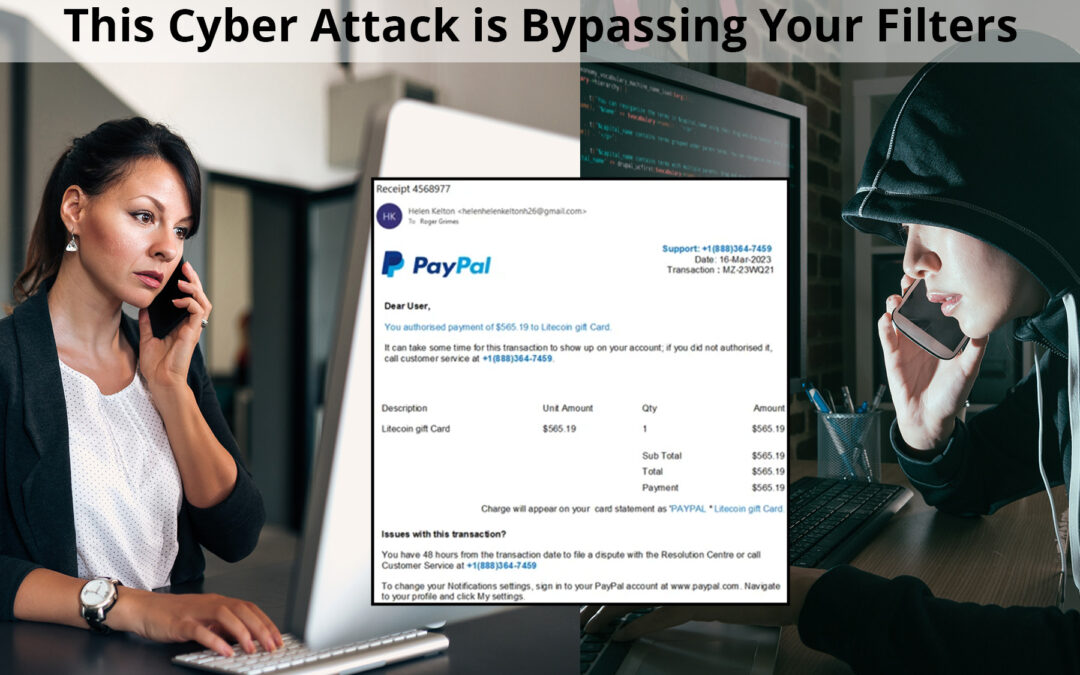
by Floyd Bell | Dec 12, 2023 | Cybersecurity
Have you heard of callback phishing? Typically a phishing email contains some sort of message requiring the user’s urgent response. But unlike traditional email phishing, it does not contain a URL linked to a malicious site or content. Instead, it contains a phone...






